Imagine going about your day, using your computer for work, entertainment, or communication. Suddenly, everything starts to act strangely. Your files are missing, your computer is running slower than usual, and you’re getting bombarded with pop-ups. What’s happening? You might be a victim of a Trojan virus.
In this blog post, we’ll get into what a Trojan virus is, how it can sneak onto your computer, and most importantly, how to detect and remove it. You’ll learn about common signs of infection and get step-by-step instructions to safeguard your digital life.
Outline
ToggleWhat Is A Trojan And How Does It Actually Work?
A Trojan virus, or simply a Trojan also called a Trojan Horse is a type of malicious software that tricks users into running it, often by posing as legitimate or useful programs. It does not spread or replicate like typical computer viruses but instead requires users to unknowingly invite it into their system. Trojans get their name from the famous Greek myth where a wooden horse was used to smuggle soldiers into Troy. Similarly, a Trojan virus hides its true purpose, and once it’s inside the computer, it can unleash harmful effects.
The goal of a Trojan virus can range from stealing sensitive data, such as passwords and financial information, to damaging or disrupting the system. In many cases, a Trojan creates a “backdoor,” which allows unauthorized users to access the infected device remotely. This could lead to more dangerous attacks, including data theft, further malware installation, or complete control of the system.
Types Of Trojan Viruses
- Remote Access Trojans (RATs): RATs give attackers the ability to take over the infected system from a distance. This access allows them to manipulate files, track activities, or even control the entire system, all without the user’s knowledge.
- Banking Trojans: These target financial data like online banking credentials, credit card information, and other sensitive financial information. They often target online banking platforms by disguising themselves as legitimate apps or software updates.
- Backdoor Trojans: A backdoor Trojan enables attackers to bypass normal authentication and gain access to a system. Once inside, the attacker can install additional malware, modify system files, or launch other attacks.
- Downloader Trojans: These are designed to download and install other types of malware. They often slip into the system quietly and then bring in more malicious software, increasing the overall damage.
- DDoS Trojans: These are used to carry out Distributed Denial of Service (DDoS) attacks. They infect numerous computers and then command them to flood a target network with traffic, causing it to crash or become inaccessible.
- Rootkit Trojans: These aim to hide the presence of other malware or malicious activities on a system. They often work by modifying system files or processes, making it difficult for antivirus programs to detect them.
- Spyware Trojans: These types of Trojans are used to spy on the user’s activities. They can track keystrokes, screen activity, or even record conversations, gathering sensitive information like passwords or private messages.
- SMS Trojans: These primarily target mobile devices, particularly smartphones. They send text messages to premium numbers, causing the user to incur hefty charges without their knowledge.
- Trojan-Banker: Designed specifically to steal banking credentials by mimicking a bank’s online portal, they can capture login details or redirect users to a fake site to capture financial information.
- Ransomware Trojans: Ransomware Trojans encrypt files on the infected system and demand payment (usually in cryptocurrency) to unlock them. Failure to pay the ransom can lead to permanent data loss.
How Trojans Get Into Devices?
Trojans often enter devices through various methods, exploiting the user’s trust or lack of security measures. They are typically disguised as legitimate software or files that the user might want or need. Below are the most common ways Trojans infiltrate systems:
- Email Attachments: One of the most common entry points for a Trojan is through email attachments. Users unknowingly download and run the malicious file believing it to be a document, picture, or other useful software.
- Phishing Websites: Attackers create fake websites designed to look like trusted ones. When users interact with these sites, they can unknowingly download a Trojan virus onto their device.
- Malicious Downloads: A Trojan may be hidden within free downloads like games, screensavers, or even cracked software. Once the user installs the program, the Trojan is unleashed.
- Infected Links: Clicking on suspicious links, whether found in emails, social media, or untrusted websites, can trigger the download of a Trojan. These links are often disguised to look like legitimate web addresses.
- Fake Software Updates: Users may be prompted to update their software, but instead of getting a legitimate update, they download a Trojan virus. This is common with unlicensed or outdated software.
- Peer-To-Peer (P2P) Networks: Sharing files through P2P networks can be risky since the files are not always verified. Many Trojans are disguised as desirable files that users want to download and share.
Once inside the system, the Trojan horse malware operates in stealth mode. It does not replicate itself like other viruses, but instead waits for instructions from the attacker or performs its programmed function. This function could involve stealing data, creating backdoor access, or spreading additional malware. Because they disguise themselves as legitimate software, Trojans malware are often difficult to detect until the damage has been done.
How To Detect Trojan Viruses On Your Device?
Detecting Trojan viruses on your device can be challenging because they often operate quietly in the background, disguised as legitimate software. However, there are several signs and methods you can use to check for the presence of Trojans.
- Unusual System Behavior: One of the most common indicators of a Trojan infection is unexpected behavior in your system. This could include frequent crashes, slower performance, or applications that start or stop without your input. If your device is suddenly much slower or freezes often, it could be a sign of a Trojan virus running in the background.
- Unknown Programs Or Processes: Check for any programs or processes running on your device that you do not recognize. Trojans often disguise themselves under unfamiliar names. You can use the Task Manager (for Windows) or Activity Monitor (for Mac) to identify unknown processes that could indicate a Trojan horse in your computer. Be on the lookout for high resource usage by unknown applications.
- Unexplained Network Activity: Trojans frequently communicate with external servers to send stolen data or receive instructions. If your device is using an unusually large amount of data or your internet connection seems slower than usual, it could be a sign of hidden network activity from a Trojan. Monitoring your network usage and traffic can help detect if a Trojan virus is active.
- Pop-Up Ads And Redirects: If you notice frequent pop-up ads or your browser being redirected to unknown websites, your device might be infected with a Trojan. While these symptoms are also common with adware, Trojans can generate these annoying behaviors as part of their attack strategy.
- Disabled Security Software: Many Trojan viruses try to disable or bypass your antivirus software to avoid detection. If you find that your antivirus or firewall has been turned off without your knowledge or if you cannot update it, this could indicate the presence of a Trojan horse computer virus.
- Antivirus Scans: Running a thorough scan with reputable antivirus software is one of the most effective ways to detect Trojan viruses. Good antivirus programs can identify and remove Trojans and other malware. Be sure to keep your antivirus software updated to ensure it can detect the latest threats.
- Unusual Pop-Up Messages Or Warnings: Sometimes, a Trojan virus may reveal itself through system messages or warnings that you did not initiate. These can include fake virus alerts or notifications that try to scare you into downloading more malicious software.
- Unusual Account Activity: If you notice strange behavior on your accounts (social media, email, or online banking) such as unauthorized access, it may be due to a Trojan that has stolen your credentials. Trojan malware is often used to steal personal information, which can lead to account breaches.
- New Icons Or Toolbars: Finding unfamiliar icons on your desktop or new toolbars in your browser could indicate the presence of Trojan viruses. These additional components are often installed without your consent as part of the malware.
By staying vigilant and recognizing these signs, you can catch and remove Trojans before they cause further harm.
Also Read: What Is RAV Antivirus And How To Remove It?
How To Remove Trojan Viruses From Your Device?
Once a Trojan virus is detected on your device, removing it requires specific steps to ensure that it is completely eradicated. Trojans are often embedded deep in the system, posing as legitimate programs, which makes removal challenging. There are several methods you can use to safely get rid of these Trojans and restore your device to a secure state. Each method targets different ways the Trojan might be affecting your system, from hidden programs to background processes.
Get Rid Of Trojan Viruses Pretending To Be Programs
Trojans often disguise themselves as legitimate programs to trick users into installing them. These fake programs may appear useful or even necessary for your system, but they perform harmful tasks in the background. Removing these Trojans requires identifying and uninstalling the malicious software.
Steps To Uninstall Trojan Programs On Windows:
- Click the “Start” button.
- Search for the “Control Panel” and open it.
- In the Control Panel, navigate to “Programs.”
- Click on “Programs and Features.” Scroll through the list of installed programs.
- Look for any unfamiliar or suspicious software that you did not intentionally install.
- Select the suspicious program.
- Click “Uninstall” at the top of the list.

- Follow the on-screen instructions to remove it completely.
- Once uninstalled, restart your computer to ensure the program is completely removed.
- After restarting, perform a full system scan with your antivirus software to ensure no residual files or additional malware are left on your system.
Uninstall Trojan Programs On Mac:
Here’s how you can uninstall programs on Mac:
- Click on the “Finder” icon from the Dock.
- In Finder, select “Applications” from the sidebar. This will display all the installed applications on your Mac.
- Scroll through the list of applications.
- Look for any unfamiliar or suspicious apps that you don’t recall installing.
- Drag the suspicious app to the “Trash” located in your Dock.
- Alternatively, you can right-click the app and select “Move to Trash.”
- Right-click on the “Trash” icon and select “Empty Trash” to permanently delete the app from your system.
- Restart your Mac to complete the removal process.
Remove Trojans That Posing As Startup Programs
Some Trojan viruses configure themselves to start automatically when your device boots up. This can make them difficult to detect and remove. Here’s how to identify and remove Trojans that pose as startup programs on both Windows and Mac.
On Windows:
- Right-click on the Taskbar and select “Task Manager” or press “Ctrl + Shift + Esc.”
- In Task Manager, click on the “Startup” tab. This tab shows all programs that run at startup.
- Look for unfamiliar or suspicious entries. If you see a program you didn’t install or recognize, note its name.
- Right-click on the suspicious program and select “Disable” to prevent the program from running at startup.

- If you confirmed that the program is a Trojan, follow the uninstallation steps from the previous section to remove it completely.
- After disabling and uninstalling, restart your computer to ensure changes take effect.
On Mac:
- Click on the Apple logo in the top left corner of your screen.
- Select “System Preferences.”
- Click on “Users & Groups” and select your user account on the left.
- Click on the “Login Items” tab. This section lists all items that launch when you log in.
- Review the list for any unfamiliar applications.
- If you find a suspicious item, select it.
- Click the “minus (-)” button at the bottom of the list to remove the selected item.
- Restart your Mac to ensure the changes take effect.
Get Rid Of Trojan Virus That Runs In The Background
Some Trojan viruses operate silently in the background, making them particularly challenging to detect and remove. These Trojans can consume system resources, steal data, or facilitate further attacks without your knowledge. Here’s how to identify and eliminate these hidden processes on both Windows and Mac devices through Task Manager.
Steps To Remove Background Trojans On Windows:
- Right-click the Taskbar and select Task Manager from the menu
- In Task Manager, go to the Processes tab. Look for any unfamiliar or suspicious processes running. If a process has a high CPU or memory usage but is not recognized, it may be a Trojan.
- Right-click the suspicious process and select Search online to learn more about it if you’re not sure about it.
- If it’s identified as malware or you cannot find any legitimate information, it may be safe to terminate it.
- Select the suspicious process and click “End Task” to stop it from running.

- Press “Windows + R” to open the Run dialog, type “taskschd.msc,” and press Enter.
- In the Task Scheduler, look for any suspicious scheduled tasks. Right-click and disable or delete any you do not recognize.
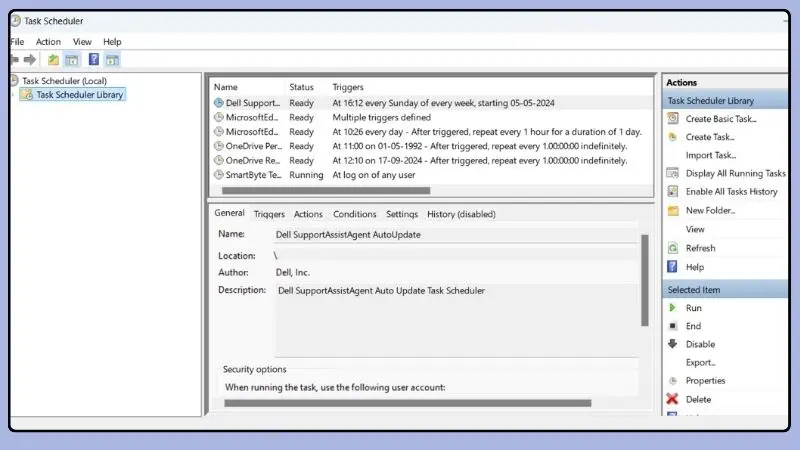
- Restart to ensure all changes take effect.
Steps To Remove Background Trojans On Mac:
- Go to Finder, then Applications > Utilities.
- Open “Activity Monitor.”
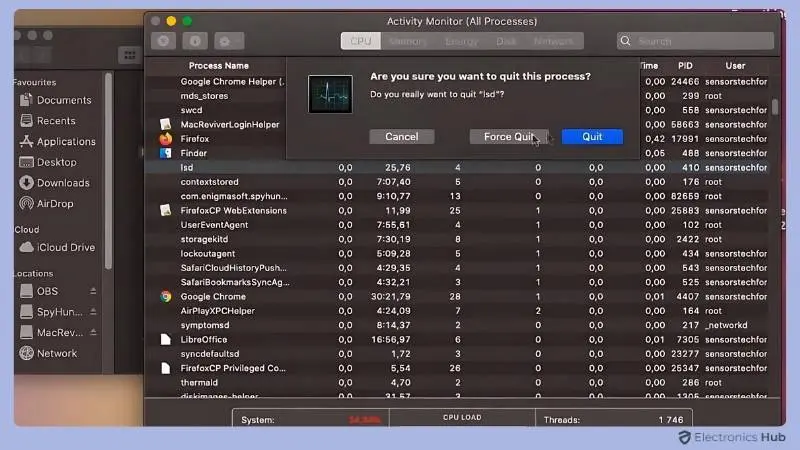
- In Activity Monitor, review the list of running processes.
- Look for any unfamiliar applications using excessive CPU or memory.
- If you identify a suspicious process, right-click on it and select “Open File Location” to see its source.
- Research the process online to determine if it’s legitimate.
- If the process is confirmed as a Trojan, select it and click the “X” button in the top left corner of Activity Monitor to force quit it.
Scan Your Devices With Antivirus Software
Running a thorough scan with antivirus software is one of the most reliable ways to detect and remove Trojan viruses. Antivirus programs are designed to search for and eliminate malicious software, including Trojans, from your device. Windows users can utilize the built-in Windows Defender to scan for malware. Below are the steps to perform a scan using Windows Defender.
- Click the Start button, then type “Windows Security” in the search bar and open the app.
- Once Windows Security opens, select “Virus & Threat Protection” from the menu on the left.
- In the “Virus & Threat Protection” section, you’ll see different scanning options. You can choose:

-
- Quick Scan: A quick check of the most vulnerable areas on your device.
- Full Scan: A deep scan of all files and running programs. This is recommended to find hidden Trojans.
- Custom Scan: If you want to target specific folders or drives.
- Select “Full Scan” for a thorough check and click Scan Now.
- The scan may take some time depending on the size of your files and hard drive.
- After the scan completes, Windows Defender will display the results.
- If any Trojans or other malware are detected, follow the recommended steps to remove them.
- Click on the “Start Actions” button to quarantine or remove the detected Trojan viruses.
To stay protected, you can schedule regular scans. Go to Virus & Threat Protection Settings, then click Manage Settings and configure periodic scans.
Perform System Restore
If a Trojan virus has infected your device and other removal methods aren’t effective, performing a System Restore can help by reverting your computer back to a previous state before the infection occurred. This method doesn’t affect personal files but will remove any applications or system changes made after the restore point was created. It’s an effective way to undo the damage caused by Trojan viruses.
- Click the Start button and type “Create a restore point” in the search bar.
- Select “Create a restore point” from the results to open the “System Properties” window.
- In the System Protection tab, click “System Restore.”

- The System Restore Wizard will open. Click “Next” to proceed.

- You’ll see a list of available restore points. Choose a restore point from a date before you suspect the Trojan virus infected your system.

- You can also click Scan for affected programs to see which applications will be removed or affected by the restore.
- After selecting the restore point, click “Next” and then “Finish” to confirm your decision.
- Your computer will restart, and the system will be restored to the selected point. This process may take several minutes.
Once your system is restored, it’s recommended to run another antivirus scan to ensure the Trojan has been fully removed.
Reinstall Your OS
If the Trojan virus is deeply embedded in your system and other removal methods have failed, reinstalling your operating system (OS) may be the most effective solution. This process wipes your hard drive and installs a fresh copy of the OS, ensuring that all traces of the Trojan virus are completely removed. However, it’s important to back up your important data before proceeding, as a clean installation will erase everything on your drive.
Steps To Reinstall Windows OS:
- Before starting, back up any important files, photos, and documents to an external hard drive or cloud storage. Reinstalling the OS will delete everything on your computer.
- Click the Start button and go to Settings (the gear icon).
- In Settings, go to the “System” tab and select “Recovery” from the options
- Select “Reset PC”, next to Reset this PC option

- You will be given two options:
- Keep My Files: This option will remove apps and settings but keep personal files. However, it might not fully remove the Trojan.
- Remove Everything: This option completely wipes the system, which is more effective for removing Trojan viruses.
- Choose “Remove everything” for a clean installation.
- The system will prompt you to either Just remove my files or Remove files and clean the drive. Choose the second option for thorough removal of the Trojan.
- After confirming your choices, the system will begin the reinstallation process. This may take some time depending on your hardware.
Once the OS is reinstalled, you will need to reinstall drivers and applications. Ensure you download trusted software to prevent future infections.
Steps To Reinstall macOS:
- Use “Time Machine” or an external hard drive to back up all important files. The reinstall will delete everything on your Mac.
- Turn off your Mac. Press the power button to turn it back on, then immediately press and hold “Command + R” until the Apple logo appears. This will boot your Mac into Recovery Mode.
- In the macOS Utilities window, select Reinstall macOS, then click Continue.
- Choose the disk where you want to install macOS. Follow the on-screen instructions to start the installation process.
- After the reinstallation is complete, your Mac will restart and prompt you to go through the setup process. You can restore your backed-up files during this step if you used Time Machine.
- Reinstall necessary apps and ensure they are downloaded from trusted sources to avoid reintroducing malware.
Tips To Avoid The Risk Of Trojan Horse Virus In Future
Preventing Trojan horse viruses from infecting your device is crucial for maintaining the security and performance of your system. Taking proactive steps to reduce the risk of infection can save you from the potential harm caused by Trojan viruses. Here are some important tips to help you protect your device from Trojans in the future.
- Use Reputable Antivirus Software: Ensure that your device is equipped with reputable antivirus software that is regularly updated. Good antivirus programs can detect, block, and remove Trojan horse computer viruses before they can cause any damage. Enable real-time protection and schedule regular system scans to keep your device safe.
- Keep Your Operating System And Software Updated: Regularly update your operating system, web browsers, and applications to patch vulnerabilities that cybercriminals may exploit to deliver Trojan horse malware. Software updates often include security fixes that protect your system from newly discovered threats.
- Download Software From Trusted Sources Only: Avoid downloading software from unverified or unofficial sources, as these are common vectors for Trojans. Always download programs, apps, and updates from official websites or trusted app stores. Be cautious with freeware and pirated software, as they often contain hidden Trojans.
- Be Careful With Email Attachments And Links: Email is a common delivery method for Trojans. Be suspicious of unsolicited emails, especially those containing attachments or links. Never open attachments or click links from unknown senders, and always double-check that an email is legitimate before interacting with its contents.
- Enable A Firewall: A firewall acts as a barrier between your device and potential threats. Make sure your firewall is enabled, as it can block unauthorized access to your system and prevent Trojans from communicating with external servers.
- Avoid Clicking On Pop-Up Ads And Suspicious Links: Many Trojan viruses are delivered through deceptive ads, pop-ups, or links on compromised websites. Avoid clicking on ads or banners that seem too good to be true, and use an ad blocker to reduce the risk of encountering malicious ads.
- Use Strong And Unique Passwords: Weak passwords make it easier for cybercriminals to gain access to your device and install Trojans. Use strong, unique passwords for all your accounts, and change them regularly. Consider using a password manager to generate and store complex passwords.
- Be Cautious With External Drives And USB Devices: Trojans can spread via infected USB drives or other external storage devices. Always scan external devices with antivirus software before accessing any files stored on them. Avoid using USB drives from unknown or untrusted sources.
- Monitor Your Device’s Activity: Regularly check your device’s performance and network activity. If your system is running slower than usual, or you notice unexplained data usage, it could indicate the presence of a Trojan virus. Early detection can prevent more significant damage.
- Educate Yourself About Social Engineering Attacks: Many Trojans are delivered through social engineering techniques designed to trick users into installing malware. Be aware of common tactics such as fake virus alerts, fraudulent tech support calls, or phishing scams. Always double-check the legitimacy of any prompts or warnings before taking action.
FAQs:
While both are types of malware, the key difference is that viruses can replicate and spread themselves to other systems, whereas Trojans disguise themselves as legitimate software and do not self-replicate. Trojans rely on user interaction for installation.
Common signs of a Trojan infection include unexpected system slowdowns, frequent crashes, unusual error messages, unexplained network activity, and unauthorized access to files or applications. You may also notice new icons or programs that you didn’t install.
Some Trojans can be delivered through compromised websites using drive-by downloads, where malware is automatically downloaded without the user’s consent. Always ensure your browser and security settings are updated to reduce this risk.
Ignoring a Trojan infection can lead to serious consequences, including data loss, identity theft, unauthorized access to sensitive information, and potential financial losses. The longer the malware remains, the greater the risk of additional damage.
Yes, Trojans can also infect mobile devices, including smartphones and tablets. They often spread through malicious apps or links. It’s essential to download apps only from trusted sources and keep your device’s security settings updated.
Phishing attempts often involve emails or messages that appear legitimate but contain suspicious links or attachments. Look for misspellings, unfamiliar sender addresses, and urgency in the message. Always verify the source before clicking on links or downloading files.
Conclusion
In conclusion, Trojan viruses pose a significant threat to your digital security. They often disguise themselves as legitimate software to gain unauthorized access to your system, potentially stealing sensitive data, damaging files, or even taking control of your device. To protect yourself, be cautious of downloading software from unknown sources, keep your operating system and antivirus software up-to-date, and be vigilant for suspicious activity on your computer. If you suspect a Trojan infection, take immediate action to isolate your device and seek assistance from a cybersecurity expert.

